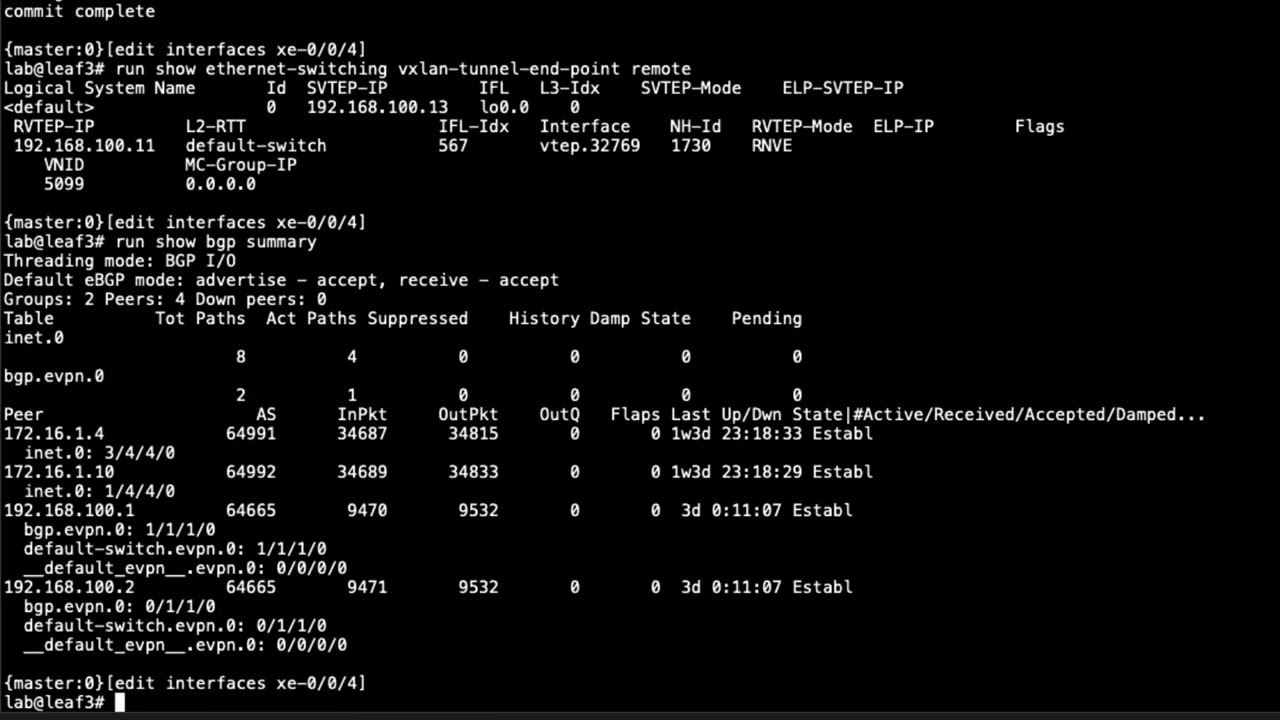
Troubleshooting Juniper Secure Connect

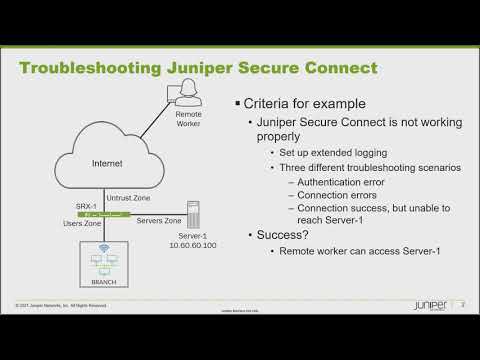
Juniper Learning Byte: The 411 on troubleshooting Juniper Secure Connect
Watch as Juniper’s Zach Gibbs walks you step by step through the process of troubleshooting broken connections using Juniper Secure Connect. If you’re new to Secure Connect, consider this essential viewing.
You’ll learn
How to troubleshoot three different scenarios: authentication error, connection error, and connection success but unable to reach server
How to enable extended logs — the first step in the troubleshooting process
How to test out connections from the remote worker device
Who is this for?
Host

Transcript
0:02 [Music]
0:11 hello my name is zach gibbs and i'm
0:14 a content developer within education
0:16 services
0:17 inside juniper networks and today we
0:20 will be going through the
0:21 troubleshooting juniper secure connect
0:24 part 1
0:25 learning byte and before i continue i
0:27 want to point out that this is part one
0:29 of a three-part series
0:31 so please when you're done with this
0:32 learning byte check out the other parts
0:36 all right so here is our example the
0:38 topology you see here might be kind of
0:40 familiar if you've gone through my other
0:42 juniper secure connect learning bytes
0:44 because it's the same one
0:45 and so what we have is we have a few
0:48 different devices we have srx1
0:50 that is connected to the user's zone and
0:54 then it's connected to the server's zone
0:56 and then it's connected to the
0:57 untrust zone now the user zone has just
1:00 your typical branch
1:01 users and then the server zone has
1:03 server one now take special note of that
1:05 ip address of server one
1:07 that is 10.60.60.100 that'll be
1:10 very important for our learning byte
1:12 today okay then the remote worker is
1:14 connecting to the internet and the
1:15 remote worker needs to access
1:17 server one and not access anything else
1:19 in the user zone we want to prevent that
1:21 type of access
1:22 and so what are we doing for this
1:24 learning fight well currently
1:26 juniper secure connect is not working
1:28 properly and so we'll do a few things to
1:30 troubleshoot this problem first we'll
1:32 set up extended logging so we can really
1:34 understand what's going on
1:35 and then we're going to have three
1:37 different troubleshooting scenarios
1:38 we're going to have an authentication
1:40 error scenario some connection errors
1:42 then a connection success but
1:44 then after that we won't be able to
1:46 access server one with the remote worker
1:48 through juniper secure connect
1:51 okay so and with this what is our
1:52 definition of success
1:54 well success is when the remote worker
1:56 can access server one
1:58 and so with that being said let's go
1:59 ahead and jump
2:01 to the remote worker and get this
2:03 started
2:06 all right so here is the remote worker
2:09 device
2:09 and what we want to first do is we want
2:11 to first configure extended logging
2:14 and if we go to the juniper secure
2:15 connect client and we select help
2:18 and then go to extended log settings and
2:21 here we are able to enable extended logs
2:24 and first we'll do the enable driver
2:26 full trace
2:27 and that's for the client vpn dialing
2:29 service and then we'll also want to
2:31 enable
2:32 extended pki logs and extended pki
2:36 interface logs as well as client monitor
2:39 client command line tool and credential
2:41 provider and you may or may not need to
2:43 restart these
2:44 uh normally you don't but if you are
2:45 having problems with this then you can
2:47 click restart
2:48 let's click ok and then let's try to
2:50 connect to the vpn but before i do that
2:53 i do want to
2:54 show that here on the side we're pinging
2:58 the server 1 ip address and since we're
3:00 not connected to the vpn right now we
3:02 can't reach it and that's
3:03 expected behavior and so here in the
3:06 client you can see it says extended log
3:08 mode it's blinking so you know it is
3:10 running in extended log mode
3:12 and before we actually connect let's
3:14 actually go back to help and then open
3:15 the logbook
3:17 and here's the logbook let's go ahead
3:18 and clear that screen
3:20 and then let's go ahead and attempt the
3:22 connection
3:24 and we're going to use our lab username
3:27 a password and immediately we get kicked
3:32 out now here you can see just in the
3:33 client you see a message that says
3:35 configuration download authentication
3:37 fill
3:38 and if you look in the logbook you can
3:40 see pretty much the same area you really
3:41 don't get a lot of good information
3:43 from something like this but if we
3:44 scroll to the right we can see that
3:46 we started to download the configuration
3:48 from the 10.111.111.1 host that's the
3:51 host we're connecting to that's the srx1
3:53 device
3:55 and then we just get told that
3:56 configuration download didn't work
3:58 because of
3:59 authentication failure and so this could
4:01 be a situation to where the user is
4:03 trying to log in and they can't they
4:04 can't do it they can't do it and so
4:05 they're upset they think there's
4:06 something wrong so they call you as the
4:08 i.t
4:08 administrator and they want you to
4:11 figure out what's wrong and so we know
4:12 that the remote worker tried to log in
4:14 just
4:14 couldn't log in and so let's go ahead
4:16 and jump to the srx1 cli
4:19 and look at the logs we're going to find
4:20 some more information there
4:23 all right so here is the srx1 cli and
4:26 let's look at the log messages
4:28 show log messages and then we'll match
4:31 on remote
4:32 underscore access
4:35 and there's one message here great so
4:37 what do we see we see authentication
4:39 field for user lab
4:40 and then it gives the vpn name which is
4:43 ravpnsdlb
4:44 uh from ip address that's the ip address
4:47 that the user is coming in
4:48 on and then we have the actual message
4:50 that we want to see invalid username or
4:52 password so what's happening here we
4:53 know the user is using the right user
4:55 name it's lab but they're using the
4:57 wrong password so we can just tell them
4:59 hey
4:59 use the right password and so this is a
5:01 way for you to find
5:03 out that the user is using the wrong
5:05 password we know the username is correct
5:07 but we know that authentication is
5:09 failing and it's got to be either an
5:10 invalid username
5:12 or password and so in this case it's
5:13 definitely an invalid password so let's
5:16 go ahead and jump back to the remote
5:17 worker device and enter the correct
5:18 password and see what happens
5:22 okay so here is the remote worker device
5:23 let's attempt to log in again
5:26 and we'll enter lab and then lab one two
5:28 three which is the correct password here
5:31 and things are looking a little
5:32 different tunnel setup that's great
5:35 and tunnel establishment and look at
5:37 that we can communicate
5:39 with the server one ip address and you
5:41 can look at the log book on the left and
5:43 you
5:43 can see exactly what happens there's a
5:45 lot of logs to go through here i'm not
5:46 going to go through every one
5:48 but if you're really interested in the
5:50 entire process this extended logging
5:52 will tell you
5:52 everything that happens it's incredibly
5:54 helpful
5:56 what we have is we have a few different
5:58 devices we have
5:59 srx1 that is connected to the user's
6:02 zone and then it's connected to the
6:05 server's zone and then it's connected to
6:07 the untrust zone
6:08 now the user zone has just your typical
6:10 branch users and then the server
6:12 zone has server one now take special
6:14 note of that ip address of server one
6:17 that is 10.60.60.100. that'll be
6:20 very important for our learning byte
6:22 today okay then the remote worker is
6:24 connecting to the internet and the
6:25 remote worker needs to access
6:27 server one and not access anything else
6:29 in the user zone we want to prevent that
6:31 type of access
6:32 and so what are we doing for this
6:34 learning fight well currently
6:36 juniper secure connect is not working
6:38 properly and so we'll do a few things to
6:40 troubleshoot this problem first we'll
6:42 set up extended logging so we can really
6:44 understand what's going on
6:46 and then we're going to have three
6:47 different troubleshooting scenarios
6:48 we're gonna have an authentication error
6:50 scenario some connection errors
6:52 then a connection success but then after
6:55 that we won't be able to access
6:57 server one with the remote worker
6:58 through juniper secure connect
7:01 okay so and with this what is our
7:02 definition of success
7:04 well success is when the remote worker
7:06 can access server one
7:08 and so with that being said let's go
7:09 ahead and jump
7:11 to the remote worker and get this
7:14 started
7:16 all right so let's go ahead and attempt
7:18 to log in with the remote worker device
7:20 and see what happens
7:29 you can see it's trying here it's kind
7:31 of taking its time that's
7:32 not what we saw when we connected last
7:35 time so there's definitely a problem
7:37 here
7:37 you can see here that it shows that
7:39 we're checking valid configuration
7:42 and it almost seems like things are
7:44 going to time out
7:45 and it did okay so what do we have here
7:48 in the client we see
7:49 https request failed failed to connect
7:53 to
7:53 that ip address that we're using port
7:55 443 timed out
7:57 and in the logs that's just kind of what
8:00 it shows too
8:00 nothing really extra in the logs here in
8:03 the client logs that is in the log book
8:05 so with that let's go ahead and jump
8:06 back to srx1
8:08 cli and see what's in the log messages
8:10 there
8:13 all right so here is srx1 again so let's
8:16 do the
8:17 show log messages match remote access
8:20 and we first see a fail message that was
8:23 a part of the other step then we see an
8:25 auth okay and then a logout okay and so
8:27 that's when we connected successfully
8:29 and then logged out successfully
8:30 so there's nothing new in there so we
8:32 can look at the log messages again and
8:34 look at
8:35 kmd or match on kmd and there is one
8:39 connection but this was the good
8:40 connection
8:41 and it shows that things went through
8:43 okay and what this log message is
8:45 actually showing
8:46 is that when we disconnected it showed
8:48 that the ipsec essays were cleared
8:50 the security association so nothing too
8:53 helpful there
8:54 but remember that the log message on the
8:56 client said it couldn't connect
8:58 on port 443 that kind of sounds like a
9:01 security zone doesn't it so let's look
9:03 at the security zone
9:09 and you can see here that the host
9:10 inbound traffic system services
9:12 is deactivated we need https
9:15 ike and tcp and cap enabled for host
9:19 inbound services for a juniper secure
9:22 connect vpn to work
9:23 so let's go ahead and activate that
9:30 and then i'll clear the log messages
9:32 just to get rid of the old logs
9:35 and then let's go ahead and jump back to
9:37 the remote worker device
9:39 and see if this changes anything
9:43 all right so here is the remote worker
9:44 device let's try to connect again
9:53 things are looking a little better
9:57 and that connection established great
9:59 and we can see we're talking with the
10:01 server again
10:01 perfect so that fixed our problem
10:05 what we have is we have a few different
10:07 devices we have srx1
10:10 that is connected to the user's zone and
10:13 then it's connected to the server's zone
10:15 and then it's connected to the untrust
10:17 zone
10:17 now the user zone has just your typical
10:20 branch users and then the server zone
10:22 has
10:22 server one now take special note of that
10:25 ip address of server one
10:26 that is 10.60.60.100 that'll be
10:29 very important for our learning byte
10:31 today okay then the remote worker is
10:33 connecting to the internet and the
10:35 remote worker needs to access
10:36 server one and not access anything else
10:39 in the user zone we want to prevent that
10:40 type of access
10:42 and so what are we doing for this
10:43 learning fight well currently juniper
10:46 secure connect is not working properly
10:48 and so we'll do a few things to
10:49 troubleshoot this problem
10:51 first we'll set up extended logging so
10:53 we can really understand what's going on
10:55 and then we're going to have three
10:56 different troubleshooting scenarios
10:58 we're going to have an authentication
10:59 error scenario some connection errors
11:01 then a connection success but then after
11:04 that we won't be able to access
11:06 server one with the remote worker
11:08 through juniper secure connect
11:10 okay so and with this what is our
11:12 definition of success
11:14 well success is when the remote worker
11:16 can access server one
11:17 and so with that being said let's go
11:19 ahead and jump
11:21 to the remote worker and get this
11:23 started
11:25 all right so let's go ahead and connect
11:27 to the vpn
11:28 and see what happens
11:39 all right things are looking good the
11:40 tunnel's being set up and the tunnel is
11:42 established
11:43 perfect however notice that we're not
11:46 able to reach that server
11:48 that ping that i have running is not
11:51 giving us anything back the request is
11:53 still timing out so we have
11:55 another problem we can connect but we
11:56 can't communicate with the server
11:59 and we can look through these logs these
12:00 logs are actually a little more helpful
12:02 now
12:02 since we have a bunch of stuff to look
12:04 through and we can see here that it
12:07 downloads the configuration
12:09 and then phase one sets up we see phase
12:12 one phase one
12:14 and then we start getting into phase two
12:16 and so yeah this is a little confusing
12:19 there's
12:20 really a lot of stuff in here but
12:22 something i do want to point out here in
12:24 phase two i want to point out something
12:26 this
12:28 these messages right here we see source
12:30 ranges 10.77.77.33
12:33 and then it says for any port oh let me
12:36 stop the logging and go back up
12:41 and then it says dst ranges destination
12:44 ranges 10.99.99.99
12:48 for any port uh zero through six five
12:50 five three five
12:52 and so if you know anything about these
12:55 logs if you've worked with this before
12:56 this is kind of something hard just to
12:58 to guess what this what the problem is
13:00 here and so
13:02 this is what we're getting for the
13:04 traffic selector
13:06 and so you might realize that
13:09 this 1099.99.0 for the destination
13:12 traffic
13:12 selector that's not the server address
13:15 and so we might have a problem with the
13:17 traffic selector so let's go ahead and
13:19 jump to the cli
13:20 of vsrx1 and do a little more digging
13:25 okay so here is the cli of srx1 let's
13:28 look at the log messages
13:31 we'll match on kmd and there's nothing
13:35 currently there and this might seem a
13:36 little confusing you might have expected
13:37 to see something here
13:39 and the reason behind it is it's not
13:41 going to
13:42 collect the log messages that we're
13:44 looking for when the user logs in
13:47 but it might collect something when the
13:48 user logs out so let's jump back to the
13:50 remote worker device
13:51 and log out of the vpn
13:55 so let's disconnect
13:59 all right so we disconnected and let's
14:01 go ahead and jump back to srx1
14:05 okay so here's srx1 again let's run that
14:08 command one more time
14:09 and you can see here we have something
14:11 of value we have a log message
14:13 and if we dig into this we can find out
14:15 more information
14:16 and so one thing i want to point out is
14:18 under traffic selector
14:20 we've got the remote id we've got that
14:24 1077-7733
14:26 then we have the local id of 10.99.9
14:31 notice that's not the server ip address
14:34 that's a problem so let's go ahead and
14:36 look into that all right so let's go
14:37 into the security
14:38 ipsec vpn
14:42 vpn name traffic selector and then the
14:45 traffic selector name
14:47 and we can see in here that the traffic
14:49 selector is configured
14:50 incorrectly so let's change that
14:55 change it to the server ip address
14:59 and commit that configuration all right
15:01 so that configuration is
15:03 committed let's go ahead and jump to the
15:04 remote worker device and test things out
15:08 all right so here is the remote worker
15:10 device let's go ahead and attempt the
15:11 connection again
15:18 and it's connecting again and did that
15:20 last time remember connected but we
15:22 couldn't communicate with the server
15:24 and look at the command prompt we can
15:27 see that we
15:28 are communicating with the server and we
15:30 have fixed that problem
15:33 so that brings us to the end of this
15:35 learning byte and also the end of this
15:37 learning byte series
15:38 and in this learning bite we
15:40 demonstrated how to troubleshoot
15:41 juniper secure connect problems so as
15:44 always thanks for watching
15:47 visit the juniper education services
15:49 website
15:50 to learn more about courses view our
15:53 full range of classroom
15:54 online and e-learning courses
15:58 learning paths industry segment and
16:00 technology specific
16:02 training paths juniper networks
16:05 certification program
16:06 the ultimate demonstration of your
16:08 competence and
16:10 the training community from forums to
16:12 social media
16:13 join the discussion